INTEGRATED SECURITY MODEL
Today, all areas of your security, including physical, electronic, and cyber, must be working in tandem to ensure your organization is safe from threats – both internal and external
WHAT IS INTEGRATED SECURITY?
The Integrated Security Model involves five elements of security: physical security, surveillance, cybersecurity, governance, and the human firewall. In the past, many of these facets of security have worked in silos within an organization. This is no longer feasible to keep organizations safe from constantly evolving threats. Each of these five elements must be working in cohesion to ensure your organization is as secure as it needs to be.
OUR INTEGRATED SECURITY MODEL
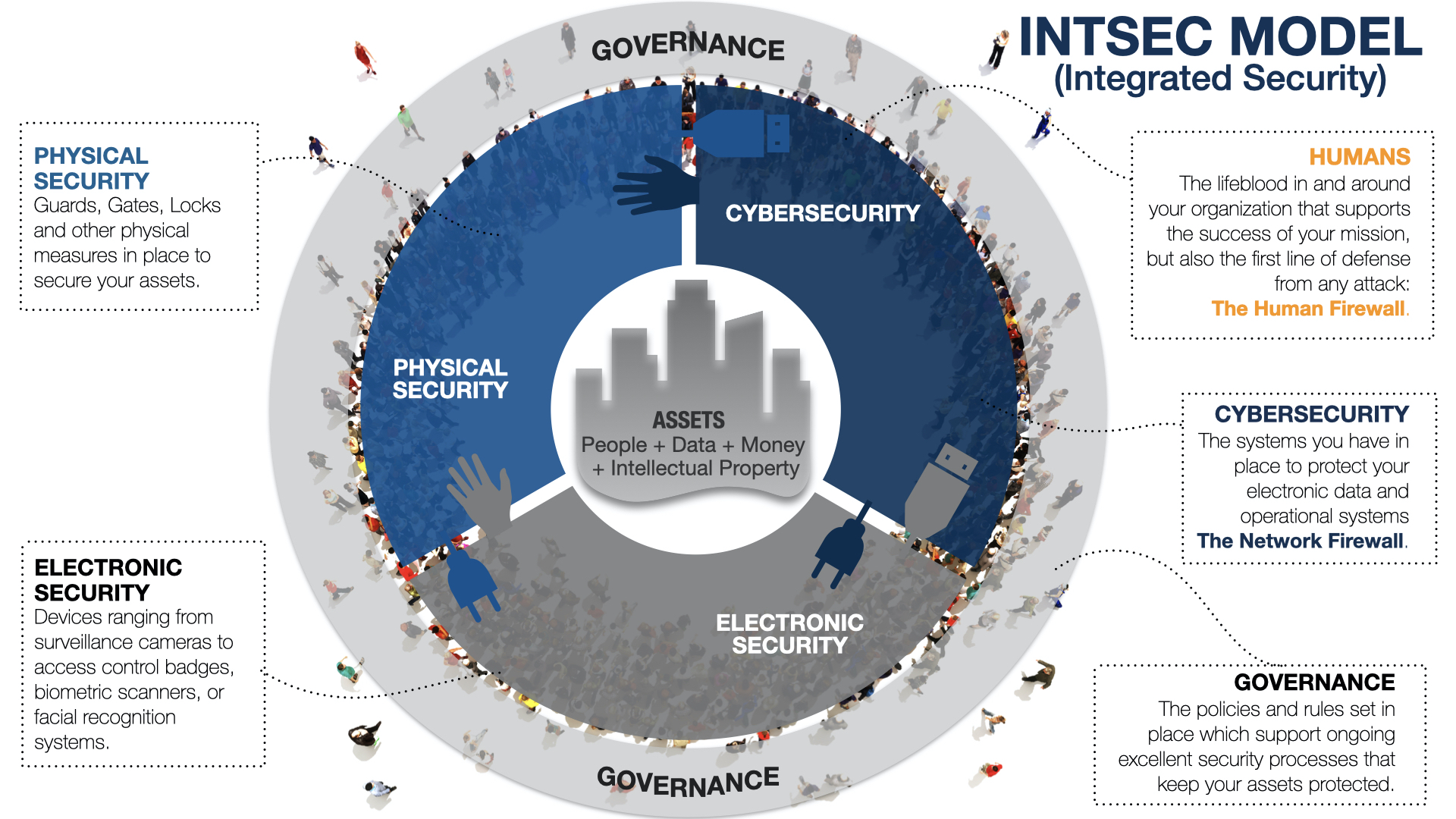
ASSESSING INTEGRATED SECURITY RISK
In our Integrated Security Model, we measure your risk in the following areas:
- Data Criticality: The value of sensitive data and your ability to protect it from loss
- Employees: The threats you face from internal sources, such as employees. These threats include the theft of IP, digital vandalism, and compromise through ignorance (e.g. team members falling for social engineering campaigns)
- Physical Security: The level of protection you have against intrusion into your buildings or datacenter
- Product/Service: Risks that your products or services can be compromised digitally
- Customers, Vendors, or Users: Risks that constituents and third parties can be compromised and impact your network, data, or IP
- Competitors: How likely are your competitors to have a willingness and the skill to attack you
- Infrastructure Security: The level of protection that your IT perimeter provides
- Regulatory: Any regulatory body that mandates cybersecurity and data rules
- Security Foundations: Do you have the basic foundations such as governance and skills
HOW WE DEVELOP INTEGRATED SECURITY
Integrated Security Design Workshop
Our consultants will come into your organization and teach your team the fundamentals of integrated security.
We will facilitate a 4-5-hour workshop to help your team understand the concepts around integrated security and provide a forum to help you determine how such a model can improve overall security at your organization.
We dive deep into the interrelationships among physical, electronic and cybersecurity services within the organization.
Your team will learn about integrated security and approaches, complete exercises so that you may consider enterprise risk management and integrated security in a practical manner as well as develop strategic next steps for the organization to improve its security posture and governance.
The results of this will improve your ability to control overall security risk at a much more granular level.
Integrated Security Risk Analysis
Our ISM Risk Analysis is typically conducted through interviewing a cross-functional team from your organization, as well as site walk-throughs conducted by our team. The outcome will be a risk report that itemizes the risk tolerance profile, current and target scores, gaps, risk improvement actions, recommendations for remediation, and possible consequences of inaction with regards to the enumerated risk areas.
By conducting a battery of interviews with key people, we delve into, at a minimum, the 10 key risk areas above.
Physical security evaluations are tailored to each unique facility; however, we will examine key physical security threat considerations including, but not limited to:
- Overall Facility Security
- Assets within Facility
- Facility Population / Size
- Facility Tenant Threat
- Design Basis Threat Evaluation
- Electronic Security
- Access Control and Perimeter Threat

